IPv6 6to4 Tunnels
- By Joe Astorino
- June 9, 2011
- 2 Comments
Introduction To IPv6 6to4 Tunnels
Right now IPv6 is a “hot” technology. It should be with the exhaustion of IPv4 address space. One common problem is that sometimes our individual site networks can upgrade or pilot IPv6 before the carrier ISP is fully ready to go full native IPv6. A similar issue would be if perhaps you want to connect to the IPv6 internet, but your ISP is not ready to give you IPv6 address space. What happens is that we can end up with several sites running IPv6 “islands”, but those islands are connected via an IPv4 infrastructure. There are a few technologies that deal with how to connect IPv6 islands over an IPv4 network, and one of those technologies is IPv6 automatic 6to4 tunnels. We will be looking at that technology in today’s blog.
Let’s say we are in charge of a corporate network. Our network has three major sites connected over a WAN in a hub and spoke topology. R5 is our HQ site and is the hub. R2 and R4 are spoke sites. R5 has frame-relay PVCs directly to R2 and R4 but R2 and R4 don’t talk directly to each other, only through the hub. Our company is interested in IPv6, but wants to pilot it between the three major sites before committing to go fully IPv6 in the future. Unfortunately, our ISP is still only running IPv4 and so what we have are three IPv6 island networks connected through an IPv4 backbone. Let’s check out the diagram and go through what we will be dealing with.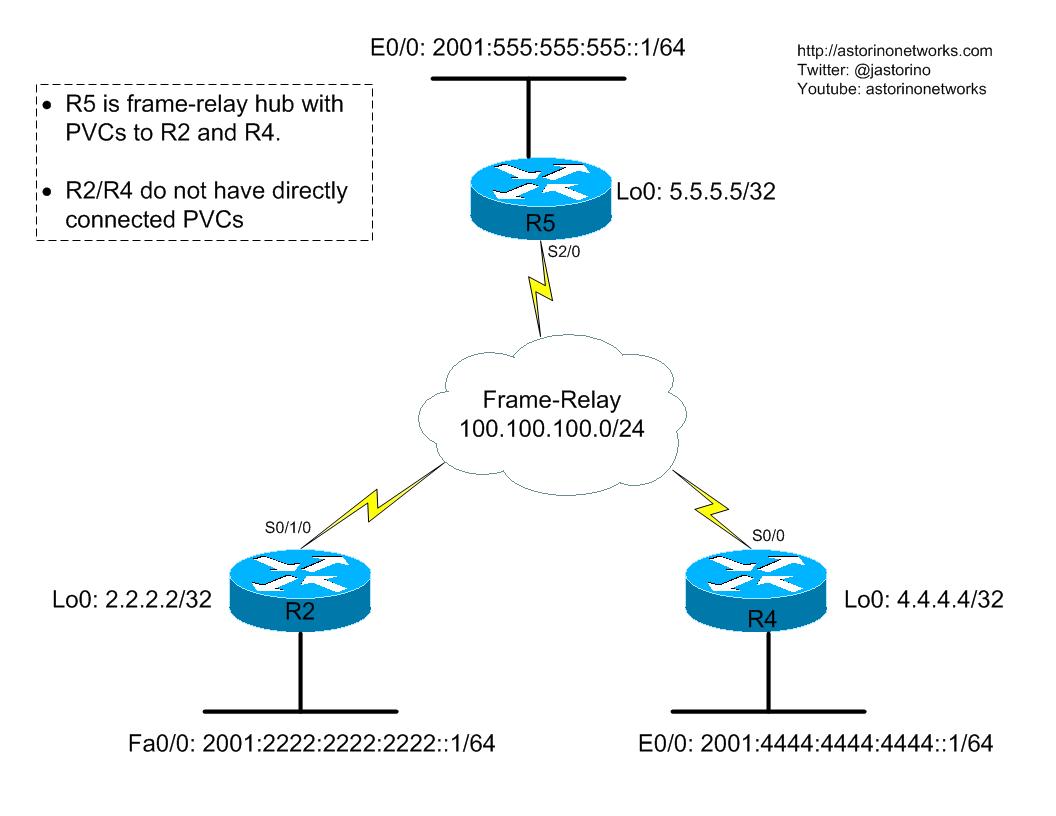
Initial Configurations
First, let’s look at our initial configurations without any IPv6 whatsoever. We will be running OSPF as our IGP over frame-relay. Each site will advertise its loopback address into OSPF. Note that the point of this blog is not OSPF over frame-relay so we won’t be covering this configuration in detail. After we look at the frame-relay and OSPF configuration on each router we will verify OSPF adjacencies and make sure we can ping the other loopback addresses to ensure we have full IPv4 reachability between our routers.
R2
interface Serial0/1/0 ip address 100.100.100.2 255.255.255.0 encapsulation frame-relay ip ospf priority 0 frame-relay map ip 100.100.100.2 205 frame-relay map ip 100.100.100.5 205 frame-relay map ip 100.100.100.4 205 broadcast no frame-relay inverse-arp frame-relay lmi-type cisco ! interface Loopback0 ip address 2.2.2.2 255.255.255.255 ! router ospf 1 router-id 2.2.2.2 log-adjacency-changes network 2.2.2.2 0.0.0.0 area 0 network 100.100.100.0 0.0.0.255 area 0 R2#sh ip ospf neigh Neighbor ID Pri State Dead Time Address Interface 5.5.5.5 255 FULL/DR 00:01:58 100.100.100.5 Serial0/1/0 R2#ping 4.4.4.4 so lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 4.4.4.4, timeout is 2 seconds: Packet sent with a source address of 2.2.2.2 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 112/114/116 ms R2#ping 5.5.5.5 so lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds: Packet sent with a source address of 2.2.2.2 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 56/58/60 ms
R4
interface Serial0/0 ip address 100.100.100.4 255.255.255.0 encapsulation frame-relay ip ospf priority 0 frame-relay map ip 100.100.100.2 405 broadcast frame-relay map ip 100.100.100.4 405 frame-relay map ip 100.100.100.5 405 no frame-relay inverse-arp frame-relay lmi-type cisco ! interface Loopback0 ip address 4.4.4.4 255.255.255.255 ! router ospf 1 router-id 4.4.4.4 log-adjacency-changes network 4.4.4.4 0.0.0.0 area 0 network 100.100.100.0 0.0.0.255 area 0 R4#sh ip ospf neigh Neighbor ID Pri State Dead Time Address Interface 5.5.5.5 255 FULL/DR 00:01:37 100.100.100.5 Serial0/0 R4#ping 2.2.2.2 so lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds: Packet sent with a source address of 4.4.4.4 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 112/115/116 ms R4#ping 5.5.5.5 so lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds: Packet sent with a source address of 4.4.4.4 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 56/59/60 ms
R5
interface Serial2/0 ip address 100.100.100.5 255.255.255.0 encapsulation frame-relay ip ospf priority 255 serial restart-delay 0 frame-relay map ip 100.100.100.2 502 broadcast frame-relay map ip 100.100.100.4 504 broadcast frame-relay map ip 100.100.100.5 504 no frame-relay inverse-arp frame-relay lmi-type cisco ! interface Loopback0 ip address 5.5.5.5 255.255.255.255 ! router ospf 1 router-id 5.5.5.5 log-adjacency-changes network 5.5.5.5 0.0.0.0 area 0 network 100.100.100.0 0.0.0.255 area 0 neighbor 100.100.100.2 neighbor 100.100.100.4 R5#sh ip ospf neigh Neighbor ID Pri State Dead Time Address Interface 2.2.2.2 0 FULL/DROTHER 00:01:49 100.100.100.2 Serial2/0 4.4.4.4 0 FULL/DROTHER 00:01:46 100.100.100.4 Serial2/0 R5#ping 2.2.2.2 so lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds: Packet sent with a source address of 5.5.5.5 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 56/57/60 ms R5#ping 4.4.4.4 so lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 4.4.4.4, timeout is 2 seconds: Packet sent with a source address of 5.5.5.5 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 56/59/60 ms
Basic IPv6 Configurations
R2
ipv6 unicast-routing ! interface FastEthernet0/0 no ip address ipv6 address FE80::2 link-local ipv6 address 2001:2222:2222:2222::1/64
R4
ipv6 unicast-routing ! interface Ethernet0/0 no ip address ipv6 address FE80::4 link-local ipv6 address 2001:4444:4444:4444::1/64
R5
ipv6 unicast-routing ! interface Ethernet0/0 no ip address ipv6 address FE80::5 link-local ipv6 address 2001:5555:5555:5555::1/64
How IPv6 6to4 tunneling works
That was a bit of leg work, but now we get to the fun part — How this tunneling is actually going to work. We have three separate IPv6 islands now, yet we are connected via an IPv4 infrastructure. Essentially what a 6to4 tunnel does is it encapsulates IPv6 traffic into IPv4 packets. The IPv4 packet will have a source address of it’s loopback interface and a destination address of the destination router’s loopback interface. The IPv4 packet on the “outside” will carry IP protocol 41 and on the “inside” will be our IPv6 packet with header and payload. Up until now, this sounds a lot like a simple ipv6ip tunnel, so what’s the difference? In an ipv6ip tunnel you specify an IPv4 source and an IPv4 destination manually on the tunnel. It is strictly point-to-point. With IPv6 6to4 tunnels, you don’t actually manually specify a tunnel destination, and the technology is multipoint. On each router we will only need a single 6to4 tunnel interface. The magic is in how that multipoint technology works, and the secret lies with the addressing. You may have to read this section a few times to get it to “click” but stay with me here.
The IPv6 prefix 2002::/16 is reserved specifically for the 6to4 tunneling technology. Your 6to4 tunnel interface will use an address from this range. Built into the address is an encoding scheme that takes your IPv4 address and encodes it into part of the IPv6 address. This works by encoding the IPv4 address into the IPv6 prefix so that your IPv6 prefix looks something like this: 2002:AABB:CCDD::/48. AABB:CCDD would be your IPv4 address. Once you have your /48 prefix you can utilize a /64 or whatever for your actual tunnel IPv6 address. When routers need to send packets to any address in the 2002::/16 range they will actually look at the 32 bits following 2002, convert them into an IPv4 address and thus figure out themselves the destination of the tunnel! Brilliant!!!
IPv6 6to4 Tunnel Configuration & Example
Whoa…yeah it sounds intense when you first learn it, but the best way to understand is with an example. Let’s look at how communication between R2 , R4 and R5 will work. R2, R4 and R5 will each have a 6to4 tunnel interface sourced from their lo0 interfaces. Each tunnel interface will have an IPv6 address assigned to it from the 2002::/16 reserved range, but we need to actually figure out what that address is. The first 16 bits will be 2002, but what about the next 32 bits? What we need to do is take our IPv4 source address and encode it into an IPv6 6to4 address. To do that we convert out IPv4 address into hex.
R2’s lo0 is 2.2.2.2. That is a 32-bit IP address. Now we need to convert that 32-bit address into hex so we can stick it into that reserved IPv6 prefix 2002::/16. 2.2.2.2 = 0202:0202. Prepend that with your IPv6 6to4 tunnel prefix to give you 2002:0202:0202::/48
R4’s Lo0 is 4.4.4.4. Converted to hex is 0404:0404 so our IPv6 prefix would be 2002:0404:0404::/48
R5’s Lo0 is 5.5.5.5. Converted to hex is 0505:0505 so our IPv6 prefix would be 2002:0505:0505::/48
Now, on each router we will configure a static route like this: ipv6 route 2002::/16 tunnel0. This says “If I need to route to 2002::/16 send it out the tunnel”. Let’s configure that and then talk through how this will work
R2
interface Tunnel0 no ip address ipv6 address 2002:202:202::2/64 tunnel source Loopback0 tunnel mode ipv6ip 6to4 ! ipv6 route 2002::/16 tunnel0
R4
interface Tunnel0 no ip address no ip redirects ipv6 address 2002:404:404::4/64 tunnel source Loopback0 tunnel mode ipv6ip 6to4 ! ipv6 route 2002::/16 tunnel0
R5
interface Tunnel0 no ip address no ip redirects ipv6 address 2002:505:505::5/64 tunnel source Loopback0 tunnel mode ipv6ip 6to4 ! ipv6 route 2002::/16 tunnel0
OK, let’s go through the communication. Let’s say R2 wants to ping R4. For now, forget about the 2001:: prefix addresses on the individual LANs for a minute. You need to understand this first. Say R2 wants to ping R4 sourced from it’s tunnel0 interface. So we have an IPv6 source address of 2002:0202:0202::2/64 and an IPv6 destination address of 2002:0404:0404::4/64. What happens? R2 looks in it’s IPv6 routing table and sees this:
R2#show ipv6 route
IPv6 Routing Table - Default - 6 entries
Codes: C - Connected, L - Local, S - Static, U - Per-user Static route
B - BGP, M - MIPv6, R - RIP, I1 - ISIS L1
I2 - ISIS L2, IA - ISIS interarea, IS - ISIS summary, D - EIGRP
EX - EIGRP external
O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2
ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2
C 2001:2222:2222:2222::/64 [0/0]
via FastEthernet0/0, directly connected
L 2001:2222:2222:2222::1/128 [0/0]
via FastEthernet0/0, receive
S 2002::/16 [1/0]
via Tunnel0, directly connected
C 2002:202:202::/64 [0/0]
via Tunnel0, directly connected
L 2002:202:202::2/128 [0/0]
via Tunnel0, receive
L FF00::/8 [0/0]
via Null0, receive
R2 has a static route for 2002::/16 so it will route the packet out the tunnel interface. Now, because the tunnel is configured for “mode ipv6ip 6to4” the router knows it needs to look at that destination address of 2002:0404:0404::4 and rip out the 32 bits following 2002 to derive the destination of the tunnel. R2 converts 0404:0404 into the IPv4 address 4.4.4.4. NOW R2 has the destination for the tunnel. R2 then encapsulates the IPv6 packet into an IPv4 packet with a source of 2.2.2.2 and a destination of 4.4.4.4. The packet is sent out our frame-relay interface to R5. R5 sees the IPv4 packet and routes it normall to R4. R4 receives the IPv4 packet. R4 recognizes that it is an IPv4 packet carrying IP protocol 41 (IPv6) so it pops off the IPv4 header and sees an IPv6 packet from 2002:0202:0202::2 destined to 2002:0404:0404::4. R4 processes the packet and replies with a packet sourced from 2002:0404:0404::4 destined to 2002:0202:0202::2.
Now the reverse happens — R4 has a static route for 2002::/16 out it’s tunnel interface so it routes the packet out the tunnel. Because the tunnel mode is “ipv6ip 6to4” R4 knows it needs to look at the destination IPv6 address to derive the destination of the tunnel. R4 converts 0202:0202 into the IPv4 address 2.2.2.2. R4 encapsulates the IPv6 ICMPv6 echo-reply sourced from 2002:0404:0404::4 destined to 2002:0202:0202::2 into an IPv4 packet sourced from 4.4.4.4 and destined to 2.2.2.2. The packet gets routed through the IPv4 network to R5 and down to R2. R2 pops off the IPv4 header and processes the IPv6 packet that was encapsulated inside.
Let’s try it!!!
R2#ping 2002:0404:0404::4 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2002:404:404::4, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 136/136/136 ms
That’s what I’m talkin’ about! Now…the cool thing is, think about what happens if I need to now ping R5. I don’t need a separate tunnel because based on the destination IPv6 address, the router will simply figure out the rest.
R2#ping 2002:0505:0505::5 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2002:505:505::5, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 68/68/72 ms
Sweet! NOW…we still don’t have connectivity to our actual IPv6 LAN blocks. That can be fixed with some quick static routing
R2(config)#ipv6 route 2001:4444:4444:4444::/64 2002:0404:0404::4 R2(config)#ipv6 route 2001:5555:5555:5555::/64 2002:0505:0505::5
R4(config)#ipv6 route 2001:2222:2222:2222::/64 2002:0202:0202::2 R4(config)#ipv6 route 2001:5555:5555:5555::/64 2002:0505:0505::5
R5(config)#ipv6 route 2001:2222:2222:2222::/64 2002:0202:0202::2 R5(config)#ipv6 route 2001:4444:4444:4444::/64 2002:0404:0404::4
To grasp this concept, you need to understand recursive routing Think about what happens if R2 wants to ping 2001:4444:4444:4444::1. R2 does an ipv6 route lookup and sees the following entry
S 2001:4444:4444:4444::/64 [1/0]
via 2002:404:404::4
The next-hop for the static route is 2002:404:404::4. For the router to know how to get to 2002:404:404::4 we need to do a recursive route lookup. We then find our static route out the tunnel to 2002::/16
R2#sh ipv6 route 2002:404:404::4
Routing entry for 2002::/16
Known via "static", distance 1, metric 0
Route count is 1/1, share count 0
Routing paths:
directly connected via Tunnel0
Last updated 00:23:44 ago
So, we send the packet out the tunnel and our encapsulation process happens again as described above. Let’s test!
R2#ping 2001:4444:4444:4444::1 so fa0/0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2001:4444:4444:4444::1, timeout is 2 seconds: Packet sent with a source address of 2001:2222:2222:2222::1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 136/136/136 ms R2#ping 2001:5555:5555:5555::1 so fa0/0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2001:5555:5555:5555::1, timeout is 2 seconds: Packet sent with a source address of 2001:2222:2222:2222::1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 68/68/72 ms
Man, this is a pretty awesome technology!
Summary
With IPv6 emerging as the new routed L3 protocol of choice, there will be situations where we need to connect IPv6 islands over an IPv4 infrastructure. Automatic 6to4 tunnels are one of a few ways to accomplish that. 6to4 tunneling works by encoding IPv4 addresses into part of the IPv6 address and uses multipoint technology

Great!! Explanation it’s helps me alot!!!!!!!!!!
When you say 32 bits from the desination IPv6 address is taken as IPv4 tunnel end point, how is it possible to take those bits from 2001::/16 address when trying to connect to 2001::/16 addresses on other sites. Or is it so that last IPv6 address that points to tunnel interface when looking up 2001:: address in the routing tables is used in extracting the IPv4 tunnel end point address? In that case I can see how correct tunnel end point IPv4 address is derived. Is that the case or there is some other mechanism?
I came to your site and you made almost all the things clear on 6to4 tunelling. Hope to get clear on the last point
Thanks.